Blockchain, cryptocurrencies, NFTs and smart contracts are all the rage. They promise (yet another) revolution. They attract public and private investment. They allow those who have embraced them to make fortunes and lose everything. They are also, however, the umpteenth step towards electronic slavery masquerading as a dream of freedom. Thanks to these technologies – but more generally to how the IT market works – we transfer control over the economic and intellectual value we create with our work and thought efforts to private operators. In exchange for what? by Andrea Monti – Initially published in Italian by Strategikon – an Italian Tech Blog. Continue reading “Stay away from blockchain and cryptocurrencies, says nerd”
The EU contradictions on cryptography
Two recent leaks reveal the European Union’s choices on cryptography. Child protection and national security are the reasons for the impossible mission of ensuring security through weakened encryption. By Andrea Monti, Adjunct Professor of Law and Order at the University of Chieti-Pescara – Originally published in Italian by Formiche.net Continue reading “The EU contradictions on cryptography”
The Dangers of Lybra
The announcement of Libra, Facebook’s crypto-currency, has provoked violent reactions and harsh criticism. Some well-founded, others less so.
by Andrea Monti – originally published in Italian
Continue reading “The Dangers of Lybra”
A Real-Life Case of Inefficient Profiling
Amazon knows in extreme detail – thanks to the analysis of purchases – my interests and – thanks to the analysis of how I use my Kindle – my reading habits. Yet he sends me an email to suggest, on the basis of my profiling, to buy a book that I wrote.
If all a giant with a limitless computing might like Amazon is able to extract from my personal data is a suggestion to buy my own books either I’m not actually monitored or profiling just doesn’t work.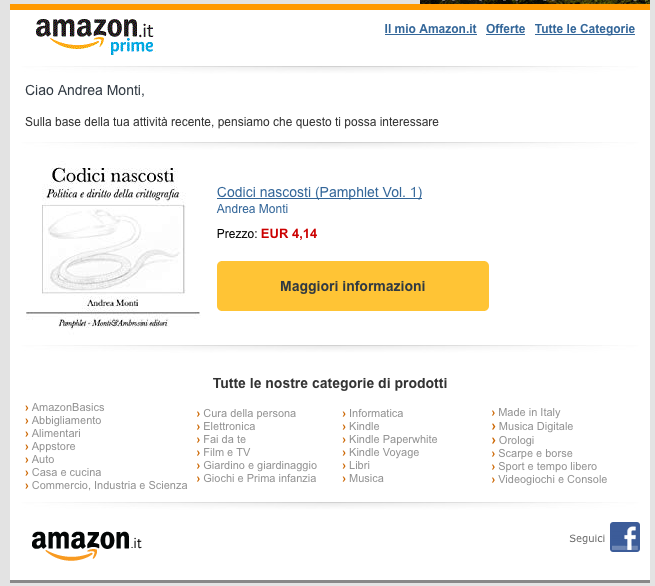
Public security, powers of the public security authority and information technology
Master of Science in Cybersecurity – Prof. Luigi V. Mancini
CYBERSURE
CYBERsecurity at Sapienza University of Rome Events
Public security, powers of the public security authority and information technology
Andrea Monti – Lawyer
?Affiliation: Adjunct Professor of Public Policy and Public Security Law at the University of Chieti-Pescara.
?May 13, 2019, from 16:15 to 18:30
?Aula II, ground floor of the building “ex-Facoltà di Scienze Statistiche” in “Città Universitaria”, Piazzale Aldo Moro, 5 (Rome).
?
|
Part 1. Technological public order and information security |
Part 2. Public security and information technology |
|
? The pervasiveness of information technologies has repercussions not solely in terms of judicial activity, but also affects the management of public order – and therefore the exercise of powers attributed to the Ministry of the Interior in different areas and before the Judiciary intervention. A modern notion of public order must necessarily take into account the issue of information security as its own constitutive element. |
This seminar describes, starting from the analysis of the Consolidated Law on public security, the structure of the public security authority, and defines roles and powers and analyses the way in which this structure deals with the subjects of the information society. ? ? ? ? ? ? ? ? ? ? ? ? ? ? In particular, it highlights the possible interactions between the State Police, Internet providers and platform operators Over the top. |
Participation is free, however registration is required on Eventbrite by searching “Public security, powers of the public security authority and information technology”.
Upcoming Seminars at https://cybersecurity.uniroma1.it/cybersecurity-seminars
For any questions or further info, please visit https://cybersecurity.uniroma1.it or write to cybersecurity_info@uniroma1.it
LinkedIn: ? ? ? ? ? ? ? ? ?Master of Science Cybersecurity Sapienza
Instagram: ? ? ? ? ? ? ? ? @cybersecurity_sapienza
