Andrea Monti – Adjunct Professor of Public Order and Security
University Gabriele d’Annunzio – Chieti-Pescara, IT – amonti@unich.it
Paper presented at the Tokyo CodeBlue Conference 2020
Abstract
This paper is about defending a person accused of computer crime and computer-related crime in Court. It is intended as a primer for those defence counsel who have no experience in the specific field of criminal trials involving computer, digital assets and the Internet. At the same time, it provides insights to computer experts wanting to enter into the digital forensics sector, because it offers a way to understand how a lawyer thinks, and what are his needs when designing a defence strategy.
The focus is on the practical issues, as emerged from the direct trial experience of the author and of other criminal trial lawyers, therefore the legal theory and the ICT technical aspects are not discussed in detail. Both the legal and the IT professional, though, can find in the discussion enough hints to widen their understanding of the matter and improve the effectiveness of their strategies.
The paper is structured in three part: a criminological profile’s taxonomy of the defendants, the analysis of the digital investigation carried on by the prosecution to build the case, and the trial strategies of the defence counsel.
Finally, a note on the cases discussed in this paper: where possible, references to court decisions are available, but in some cases, for confidentiality reasons, the paper analyses the relevant elements without providing further information.
1 Introduction
Each legal system has its own particular provisions regarding computer crimes (for instance: when a trespass is ‘illegal’, what constitutes ‘damage’ of digital goods, when an action is protected by free-speech), as well as its own rules of evidence, and therefore, it is not possible, at least in this paper, to analyse them all. There are, however, some general issues that are relevant regardless of the law of a specific country, based on the fair trial and presumption of innocence principles. These two principles are of particular importance during the investigation and for the assessment of its result for the trial.
As in all other crimes, a fundamental aspect affecting the defence of a suspect or a defendant is the motive that led him to commit the act. His drive may have been a political or ideological creed, or he may be a common criminal or a ‘normal’ citizen believing that he did not make ‘anything wrong’ in selling codes and hardware to decrypt the streaming of football matches broadcasting. Therefore, a lawyer must firstly have a reasonable knowledge of the ecosystem inhabited by hackers, computer criminals, lone wolves and ordinary people who decide to commit computer crime.
It is also crucial to know how the world of the Internet services works and how police forces collect the information necessary for their investigations. Telephone operators, Internet Service Providers (ISP) and over-the-top platforms hold important and sometimes decisive information. Sometimes they are even too eager to cooperate with the law enforcement entities, sometims they raise a barrier of legal firewall to deny their support or at least delay and limit the extention of their involvement, at least publicly.
Computer-related trial advocacy is a matter in itself, and computer-crime advocacy is a very special subcategory. A sound criminal litigation experience is of course useful, but can not be translated as such in the realm of digital crime. The topic is vast and would require a treatise to be thoroughly analysed. For now, it is important to warn the counsel wanting to try a computer-crime case that in addition to his traditional counterparts (law enforcement, public prosecutors and, sometimes, judges), his client and his expert witness are the main threat to reckon with. The former, in the case of a skilled person, may be prone to challenge his own defence counsel if he feels the inability to grasp the technical complexities of the investigation. The latter, in particular if lacking of academic credentials, may try to bring in his personal views rather than objective information, losing the focus on what is necessary for the trial. Therefore, the ideal counsel should have a solid technological background or at least the capability to understand on his own the general aspects of the digital environment so to properly address —and keep at bay— both the client and the expert witness.
2 A taxonomy of the defendant’s profile
The use of computers and telecommunications networks for criminal purposes has increased thanks to the spread of knowledge of methods and techniques outside the original hacker environment and to the lack of attention that ICT companies have paid for a long time to computer security. Action that, in the early nineties, required highly skilled computer expert, are now available as software tools or even in an ‘as a service’ business model.
Although there have always been illegal uses of information technology, the first phenomena of unauthorised attacks on computers and software are manifested in the USA in universities as a form of protest against the limitation of access to computer centres and software (Levy, 2010).
The US played a central role in shaping the hacker culture that grew up as an articulated and not necessarily coherent ecosystem. Reading its fundamental texts, similar but not entirely overlapping ideological positions emerge. The GNU Manifesto (Stallman, 1985), at the base of the free-software movement, supports a political vision aimed at eliminating the proprietary approach to software. The Conscience of a Hacker (The Mentor, 1986) theorises the hacker’s anarchic right to access any system in the name of knowledge and despite any law. A Declaration of the Independence of Cyberspace (Barlow, 1996) is a program for the creation of a new social contract based on a non-place (cyberspace).
At the same time, ambiguous figures like Kevin Mitnick, on the one hand, embody the ideal of the anti-system hacker but, on the other, propose a socially amoral model according to which if something is possible, then it can be done, no matter what.
In Europe, the hacker culture develops particular traits. One strand comes from videogames, grows around the concept of ‘just for fun’ and only later evolves toward a vision similar to that of The Mentor. At the same time, from the dystopian ideology of cyberpunk, groups are born that use hacker knowledge for political goals and are the predecessors of modern hacktivists (Chiccarelli, Monti, 2011). In Northern Europe, the German Chaos Computer Club combines considerable technical expertise with a strong political commitment to claim a rights-friendly use of information technology. In Eastern Europe, on the other hand, arise more typically criminal phenomena linked to the writing of viruses (Mungo, Clough, 1993), phishing and other forms of fraud (McCombie et al., 2009.) The European phenomenology is much more complicated, but these hints are useful to understand that there is a fundamental difference between actions carried out by people who worship a political idea or an ideological creed, and those carried out by people who ‘simply’ commit crimes using specific knowledge, not unlike forgers or drug manufacturers. Finally, we must consider the ‘lone wolves’, and individuals without a specific knowledge or motive, who often operate in the field of intellectual property infringement, producing software cracks or online streaming services.
For the sake of completeness, but it is a subject not covered by this paper, it worth mentioning the use of hacking techniques for strategic purposes by the military and security apparatuses of the States, or by groups not formally belonging to governmental bodies, but which operate (also) in the interest of a specific nation nonetheless.
Understanding the profile of the client (either a suspect or a defendant) is crucial. It is useless and inefficient to defend a political activist using a strategy designed for a common criminal or a member of a syndicate and vice-versa. In the same way, the counsel will certainly err in his assessment if he treats a lamer as if he were dealing with a real expert.
Finally, as in all types of crime, it is necessary to understand whether the accused can withstand the pressure of the trial and whether he knows how to practice the fundamental virtue of the suspect: to speak only in the presence of the lawyer, and only when the lawyer considers it appropriate.
The criminological and psychological profile of the client also play a fundamental role in the interaction between him and the police forces. A hacktivist, once identified, could publicly claim the action, valuing the media exposure more than a trial strategy based on silence and tactical actions. A subject who lives in a state of isolation from society, or who has committed crimes without belonging to criminal underground, could immediately collapse at the mere sight of uniforms and confess everything on the spot. In some jurisdictions, the statements of the suspect released without his lawyer are not valid in a trial. This ban, though, does not apply during the investigation, and therefore the prosecutor will nonetheless take advantage of the information that he has managed to collect.
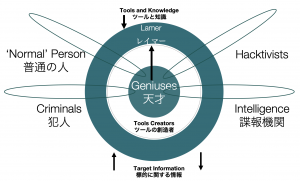
The following graph is a synthetic but precise description of how the ecosystem of the digital underground is composed and where the hacker world intersects with the world of crime and intelligence. It is useful because it allows the lawyer to position the accused in a reasonably precise location and facilitates the work of setting up a defence consistent with his criminological profile. Wanting to summarise, therefore, one can say that a hacker is not necessarily a criminal, and a criminal is not necessarily a hacker.
3 The analysis of the investigation’s file
Very often, the lawyer is involved in the early phase of the investigation, either when the police arrest the suspect or when they seize his computer and everything available to him. When this happens, it means that the prosecution has reached sufficiently robust clues to identify at least the place where the criminal action started.
Depending on the jurisdiction, the due process principle requires the discovery of these acts of investigation. In the European Union, Directive 13/2012 makes mandatory for the public authorities to inform the arrested person about the charges and the evidence against him. He can also obtain all the elements that led to his identification yet in the investigation’s early phase.
A word of wisdom: also if the acts of investigation are all logically linked and the evidence seems to be very strong, there could be grains of sand (sometimes as big as mountain rocks) that block the investigation machine. A criminal trial is like Swiss-cheese: it is full of holes that the public prosecutor, subjected to the ‘innocent until proven guilty’ principle, has the duty not to leave open, but that the defence counsel has no obligation to plug.
The next paragraphs go into more detail on the management of the investigation of a computer-crime suspect but it is not possible to cover them all. However, the volume Searching and Seizing Computers and Obtaining Electronic Evidence in Criminal Investigations (Jarrett et al., 2009) offers more comprehensive information to read with the eyeglass of the defence, rather than with those of the prosecution.
3.1 Outcomes of the crime scene investigation
As soon as it becomes available, the defence counsel should check the investigation dock to find how the victim of the crime discovered the fact, and what he or she did as soon as he or she understood what had happened.
When an individual realises that he has undergone a cyber attack, after trying unnecessarily to remedy it on his own, he will most likely turn to some private technician and only then, finally, to the police. In other words, the attacked computer will arrive in the hands of investigators already widely manipulated, without any control over the integrity and non-alterability of the data it contains.
In other cases, the victim only provides the police with printouts of emails or web pages, or he will show his smartphone to hand them the contents relevant to the investigation.
While all this is useful in the preliminary phases, police cannot just take what the victim says for granted. So, they need to make technical checks on the attacked hardware to gather as much objective evidence as possible. If the crime is serious, this is likely to happen; but in minor cases such as phishing, defamation or malware infection often the investigators do not go beyond a cursory look. The missing links in the chain of custody may support the later challenge, at the trial, of the evidentiary value of the digital forensics analysis.
The issue becomes even more relevant when the attack has hit institutional or industrial targets. Odd as it may seem, a corporate environment might lack crisis units for the management of cyberattacks, and when there are, they might not have forensic-oriented skills. It is highly probable, therefore, that police receives information which is the result of analyses carried out directly by the IT security team or even by an external consultant, without adopting any digital forensics care. Furthermore, if the victim uses a cloud or a SaaS (Software as a Service) platform, these data may not be available at all. That might happen, for example, because the service contract does not provide for the storage of security logs, because there is no contractual obligation to keep it for a specific time, or because the provider has no interest in sharing it with the customer, to avoid being accused of breach of contract or tort.
Although investigators should collect and analyse all these data by themselves, it does not always happen. In order to save time and resources, they can have the digital forensic delivered directly by the victim without replicating it by themselves. Therefore, the defence counsel will have to check where the technical assessment came from and who handled the information that the police used to identify the place where the attack started and all the results of the investigation.
The preliminary results of the investigation allow a place to be identified but not necessarily a natural person. This remark must not be under-evaluated: even though police is confident that the action started from a precise location, this does not necessarily identify the perpetrator. If therefore, the suspect has kept silent and made no admission, his position is not necessarily compromised.
In a case of possession of child pornography decided in Italy by the Court of Sulmona several years ago, the Italian police had identified the apartment from which the download of the illegal contents started. Accessing the place, however, police faced the unexpected. There was only one computer in a common area. Moreover, all the students who lived there just used one shared account. Finally, the police simply took away the computer without taking the keyboard and mouse from which they could have obtained biological samples and fingerprints that would have been useful to identify the culprit. At the trial, the judge acquitted the defendant because there was no beyond reasonable doubt evidence that he was the actual computer’s user involved in illegal activities.
Such an outcome is an example of why a criminal trial is like Swiss-cheese: it was the prosecutor who had to close the holes, while the defence attorney merely pointed out that they were still open during the trial.
3.2 Traffic data and IP assignment
In parallel with the crime scene analysis activities, the prosecution tries to collect information from telephone companies and ISPs on the internet traffic data associated with the attack. If the analysis of the logs of a network appliance retains an IP number connected with the attack, the investigators can look for the ISP that allocates such IPs. There is no need to get a warrant or activate a Mutual Legal Assistance Treaty (MLAT). The information are publicly available and it is enough to query the Whois databases of the five entities that manage the assignment of IP numbers to telco and internet operators (ARIN, APNIC, RIPE, LACNIC, AFRINIC). Until a few years ago also the identity of a domain name assignee was (mostly) available in the same way throughout the various domain registrar. Now it is not possible anymore because suddenly raised ‘privacy concerns’ and, in the EU, the compliance with the General Data Protection Regulation, made all of these information go confidential. The result is that if a domain assignee is handled by a foreign registrar, there is no alternative for the prosecution but to activate an MLAT request. This is a major problem for the prosecution because without a valid court order no foreign entity will disclose information to the authority of another country. The counsel must pay the utmost attention to the source of the information used by the prosecution, as the lack of a proper formal acquisition might jeopardize the further exploitation in the upcoming trial, under the ‘poisonous fruit’ doctrine.
The next step is to ask the IP assignee operator which customer is using it: this is a critical step because the prosecution should check that at the time of the request the IP number involved in the attack was always used by the same customer (mind, customer, not a specific individual.) In some cases, ISPs do not provide such details and just deliver the name of the subscriber. In other cases, however, they spontaneously provide more detailed information. Therefore, it is essential for the counsel to check whether or not the suspect held the IP number at the time of the offence by carefully reading the messages exchange between the police and the ISP.
One of the holes in the digital Swiss-cheese that investigators rarely plug is spoofing or, in broader terms, the use of IP number alteration techniques. These techniques allow to trick the computer to which the attacker wants to connect, letting it record an IP number that is not the one the attacker is using, and that will, therefore, mislead the investigators.
It is uncommon for the prosecution to go into these aspects in-depth. If the outcomes of the search and seizure at the suspect’s premises provide just the faintest confirmation of the latter being the culprit, the prosecution would not waste more time to pursue other investigative paths. If, however, if the search and seizure are unsuccessful, then the correctness of the IP communicated by the Internet Service Provider becomes an issue. Moreover, if the suspect has kept silent, it is the prosecutor who has to justify why that specific IP number would be evidence against the former.
The difficulty of obtaining accurate information about the Internet traffic data grows because of the frequent use of dynamic IP addressing, a technique of temporarily assigning a network address from a block of addresses to a user for the duration of a single session.
Examining the logs held by the individual’s IAP is the only way to make the relationship between a dynamic IP address and an individual user. Answering this question usually requires a sophisticated analysis of logs, accessing several databases, authentication servers, firewalls, and other equipment. which seldomly can provide data integrity and non-refutability (Monti, 2004.)
A further difficulty in the use of IP for the identification of the perpetrator of a crime are the Wi-fi connections accessible without authentication credentials such as those offered in fast-food or public places. The fact that the suspect had been seen, perhaps by surveillance cameras, near a particular pub where the attack started does not necessarily mean that he was using that IP number at that specific moment. Without evidence that can come from a search of the suspect’s computer or smartphone, the simple, abstract possibility of using a specific IP is not enough to support identification. The defence counsel should, therefore, carefully verify the motive that supported the association between the fact, the IP number and the suspect.
This is not enough, though, as the defence counsel must also check whether the police-collected traffic data are consistent with the crime. If, for example, the attack was against an FTP account, but the traffic data associated with the accused at the time only record HTTP connections and to other IPs, it is highly likely that the association between IP and assignee is wrong. This is an example of the ‘torpedos’ that the defence attorney will launch when the trial is started and the prosecution has no way to deflect the blow. Unless, like in many EU countries, there is an obligation to retain traffic data long enough and the trial goes quickly, it is likely that by the time the judge orders to verify whether the defendant had that particular IP number available, the data disappeared forever. The trial will lose an essential piece of evidence.
There is one final aspect that defence counsel must consider when analysing the traffic data: the way the investigators collected it.
The defensive usefulness of this check depends on the rules of evidence of the individual jurisdictions. In short, this is the point: when investigators need the data that is available to ISPs, they can do two things: they can obtain a warrant issued by the prosecutor or the judge, summon the suspect with his lawyer and a trusted expert, access the ISP’s IT systems, extract the information and give a copy to the suspect for his own forensics analysis. Unless the needs of the investigation require secrecy, this is the correct way to proceed: all parties are present and verify that the data has been recovered and stored correctly. Alternatively, instead of following this procedure, the police may just sends an email to the ISP, perhaps without even attaching the magistrate’s order, and have the data sent back to them.
The difference between the two cases is evident: in the first case the rights of defence are fully respected; in the second case they are not, because technical operations are carried out by a subject, the ISP, without any supervision or control, not even by the judiciary. Such was the standard often followed by prosecutors in Italy, and which a judge declared invalid as early as 2005: … The investigation has been executed without more in-depth findings, because [the Postal Police] just asked the ISP without any formal acquisition of the data and without any check about the data freezing to guarantee the evidentiary value in term of integrity and reliability over time. (Criminal Court of Chieti, Decision No 175/05).
3.3 Digital forensics issues
The intricacies concerning how to recover traffic data held by ISPs also arise for computers and storage media seized from the suspect. Police forces have not always given due importance to the chain of custody, also when handling digital information. Superficial behaviours such as, for example, browse the seized computer without caring for possible alteration of the information contained, or copying data to rewritable media without caution are not uncommon. In one case, the suspect deleted all the contents of his clients right in front of the police that was seizing his computers, because nobody ordered him to stop using his computer.
The negligence of investigators in the execution of seizures and analysis of computers has given rise to a line of defence, much supported by computer experts (and equally bashed by courts), according to which computer forensics analysis performed without respecting the computer forensics’ best practices produces unreliable results. A similar defensive strategy is to argue that a regular file found on the suspect’s computer or delivered by the victim has no value as evidence because anyone could have created it.
The first defence, the one based on contesting the ‘method’ even before the results obtained, is not new and was immediately limited by jurisprudence. Since 1997 the US Courts have held that ‘[m]erely raising the possibility of tampering is insufficient to render evidence inadmissible’ (United States v. Allen, 106 F.3d 695, 700, 6th Cir. 1997).
The practical effect is that the defendant bears the burden of proving tampering or unreliability of digital evidence. In order to properly balance the need for efficient resolution of justice, with the rights of defendants to the presumption of innocence and fair defence, decisions that convict persons based on evidence obtained via less than arduous forensic procedures must not be endorsed (Kennealy, Monti, 2005).
At least in the EU, though, the Budapest Convention on Cybercrime partially changed the scenario, opening a new opportunity for a procedural defence. A decision of the Italian Supreme Court dismissed the relevance of the compliance to computer forensics best practice in managing digital data but also held that preserving their integrity is mandatory.
There is no such thing as a standard for the methodology to process and analyse computer evidence … concerning which the only mandatory principle is that relating to the preservation of the integrity and non-alteration of the physical traces of computer data, to be ostended at the trial and analysed through the copy of the same obtained through a procedure that ensures its correspondence with the original (Supreme Court Criminal Section, Judgment of 6 September 2012 no. 44851).
The lack of compliance with the principle settled by the Budapest Convention re-opens the possibility to challenge the evidentiary value of computer data that are not adequately secured. In this case, the procedural challenge is more robust because it is based on the infringement of a legal rule, rather than upon what is perceived as a speculation.
This line of defence should push the Court into stating that the lack of compliance with the best practice affects the admissibility of the evidence and not only its ‘weight’. The defence counsel could refer to the decision of the Italian Supreme Court that, in a case that gained the front-page of media around the world, acquitted in 2015 Amanda Knox from the accusation of having killed together with her then-boyfriend, Raffaele Sollecito, her friend Meredith Kercher. The Court is adamant in stating that the lack of compliance with scientific protocols internationally validated, deprives the results of any evidentiary value whatsoever. They can enter into the trial, but do mean nothing (Cass. pen., sez. V, sent. 25 March 2015, n. 1105). The merit of the decision was about the genetic samples found on the crime scene, but the principle expressed by the Court is valid, by analogy, for digital evidence too.
The second defence, the one based on the fact that anyone could have entered a content found on a computer, has long been considered unpresentable because of its extreme speculative nature. However, the internationally renown case of Hacking Team, the Italian company producing malware able to take control of computers and smartphones, and made available to many countries also not precisely democratic, and the use of computer trojans by law enforcement and judiciary powers around the EU re-proposes the problem. The defence will seldom have the chance to prove that a particular object has been inserted in the computer by someone else. Therefore, it should be the prosecution’s duty to show that all stages of the investigation followed the rules, acting also to protect the right of defence.
As in the previous case, the aim is to attack the method and not the result, but given the attitude of the courts, without a law to support this defence, it is unlikely for a court to sustain it.
3.4 Covert operations
Online covert operations are essential for the investigation of all those crimes based on the existence of a ring, from child pornography to copyright infringement, to terrorist or criminal groups. Also, in this case, the way of using this method of investigation changes according to the different jurisdictions, nevertheless, it is possible to give some general indications for the defensive strategy.
It is highly unlikely that the authors of the transaction meet in person and therefore, typically, the exchange of digital content takes place at a distance. Such modus operandi facilitates the work of investigators who can more easily infiltrate the ring or otherwise come into direct contact with the suspect. At the same time, though, this method is prone to mistakes that the defence can later exploit.
Usually, the exchange of illegal content takes place after having build a trusted relationship with the other party. The prosecution holds the transaction and the circumstantial (digital) information as the smoking gun and the probable cause to further proceed with the investigation. The nest step, therefore, is to look for information at the ISPs and then proceed with searches and seizures looking copy of the exchanged material. It is precisely now that for the defence spaces can open up.
The banknotes used to pay a ransom bear invisible marks in such a way as to be traced and recognisable. The same method, however, seldom applies to the exchange of digital contents and in particular to those sent by law enforcement. If the contents are ‘commonly’ available online and the officer forgot to apply steganographic or similar markings, it will be more challenging to prove that the file found on the suspect’s computer is the same of the exchange. To provide such evidence becomes even more complicated if the file in question, found on the suspect’s hard drive, was created on a different date (because perhaps the date on the accused’s computer was not set correctly) and/or found in a different directory from the one where the software used for the exchange usually keeps the files received.
Although it was not the reason why the accused was acquitted, this defence was effective in a child pornography case, where the judge criticised the police investigative technique:
Since the operating officers did not take adequate measures to ensure the identity of the file transmitted … the expert correctly pointed out that the files found under the directory as mentioned above cannot be identified in a technical sense as the same object of transmission by the law enforcement but as files of identical content (Court of Civitavecchia, Criminal Branch, decision no. 1277/04.).
Also, the evidence that the file has been locally executed is another important factor because helps to identify the mens rea. How can the prosecution affirms the guiltiness of the suspect if he did not open the incriminating file and therefore he did not have knowledge of his content?
Another element to take into account when analysing the prosecution dock is the identity of the person who initiated the exchange. If it was the suspect who spontaneously proposed to send the illegal material (and it is possible to prove that he was the one using the computer), it is one thing. However, if it was the investigator who pushed the accused to make the exchange and break the law, the scenario changes completely. That is why carefully reading the transcripts of the chat or messages that the investigator exchanged with the accused can provide some extra weapons to the defence.
4 The Trial
The main mistake of inexperienced prosecutors and defence counsel is to base their trial strategy exclusively on digital evidence, ignoring the importance of physical evidence, logic and common sense. The lack or weakness of digital evidence, indeed, can be overcome by other ‘traditional’ findings that reinforce the value of the electronic clues. Relying solely upon digital evidence may nonetheless be a strategy, but the choice must come after a thorough assessment of the case dock and not by ‘inspiration’ or —worse— by the eagerness of showing how learned is the counsel.
The following example clarifies the point: a defendant charged of defamation via a social network, claimed not to have been the user of the smartphone used to publish the content. The prosecution had already established that the defendant was the assignee of the phone number, that he was its owner at the time of the publication of the insulting post, as the smartphone had access to his social network profile. The digital evidence may be uncertain because there is no proof that the defendant was using the phone in the moment of the publication, but the prosecution offered also another evidence: the content of the post was related to facts that only the defendant could have known. This last ‘traditional’ evidence weighted enough to overcome the uncertainty of the digital part of the investigation, and the verdict was against the defendant.
The procedural defence whose purpose is to challenge the evidence-gathering process and not the results achieved is essential in computer crime cases.
US Courts have dealt with many of such issues and their findings can be a guidance for all the parties of the trial. Still, every jurisdiction has its own peculiarity so, until the definition of clear criteria on how to collect and manage digital evidence, the procedural defence is a necessary part of the defensive strategy.
The difficulty to put it into practice are mainly two: the counsel must be well versed in the IT aspects of the investigation, and solely relying upon legalistic matters usually conveys to the judge and the prosecutor the sense of an indirect admission of guilt. The wording of a 2007 decision of an Italian court can not be more explicit:
the conclusion seems irrefutable to us, despite the arguments put forward by the defence which, evidently, aware of the seriousness of the evidence collected by the Prosecution, has moved exclusively with procedural objections, trying to get all the technical investigations carried out by the Police out of the trial.
As much as a defence counsel might dislike it, then, in court pragmatism rules:
Prosecutors want to win, especially when a guilty defendant tries to get off because of some governmental misconduct and a technicality. In such cases, the law demands acquittal. … Prosecutors … often seek convictions in cases based on illegally obtained evidence. In such cases, the prosecutors are not seeking justice. They, like the defendant who wants an acquittal, are seeking only one thing: to win (Dershowitz, 1989)
Therefore, the lawyer must be cautious in using a procedural defence to challenge how the prosecutor achieved his results and their evidentiary value, to avoid being accused of ‘wild speculation’ and thus deadly affecting the case, in particular, if there is a jury listening.
Deciding to go for a procedural defence, then, suggests to confront directly the matter, by making a point in terms of defence rights:
If we permit laziness in the application of forensic procedures, we either focus attention away from the substantive interpretation of laws applied to novel controversies or preclude tackling substantive interpretation because of muddied procedural waters (Kennealy, Monti, 2005).
Another component of the trial strategy is the exploitation of the Swiss-cheese principle.
Knowing how the digital world works allow to highlight missing links in investigations. For example, the IP number assigned to the accused was communicated to the investigators by the ISP, but they did not verify whether the ISP handed out the correct data. Or the prosecutor seized the computer that the accused used to commit the crime, but no one verified if the computer was functioning at that time, or if it could connect to the network. Or, moreover, the charge is that of spreading a virus, but no one has verified whether the infected computers were actually damaged. Countless are the example of how the Swiss-cheese strategy comes into play: the defence counsel spot the ‘holes’, plug them is a prosecutor’s duty.
Mens rea is the third path of a defence. Its ascertainment, not only in the computer crime’s trials, is very complicated. Actions and their consequences are ‘measurable’, but proving the mental attitude of the accused is not always easy or possible. Nevertheless, mens rea is fundamental to establishing the defendant’s innocence or guiltiness. In other words, it is not enough for a provision to state that the illegal access to an IT system is a criminal offence, but it is also necessary to specify whether the crime is committed because of a voluntary act or also by mistake or recklessness.
In a case of illegal access to an Italian bank, the Criminal Court of Milan (IT) acquitted the defendants because they had committed the fact by believing that the penetration test contract between the bank and the multinational software company for which they worked was already active: the fact was there, but the mens rea was not.
Finally, some thought about the relationship between the defence counsel and the judge.
First of all: a judge rarely agrees to be lectured by a lawyer, especially if the latter is also an academic. Often, however, computer-crime trials require the counsel to introduce in the cross-examination and its objections some technical aspects that are most likely little known to the judge, and about which, perhaps, the prosecutor will have to dispute. It is essential, therefore, to find the right balance between the need to pass on the information to the court and the importance of not highlighting the judge’s lack of knowledge, or appearing as patronising him.
Furthermore, the lawyer must have respect for the intelligence of the court. The lawyer should not deliberately try to confuse the judge by exploiting his unfamiliarity with information technology to present arguments that are just wild speculation or to generate confusion and lengthen the duration of the trial. The judge may not be an information technology expert, but he is perfectly capable of understanding when a lawyer is trying to be ‘smart’.
It is a suicide strategy that can only harm the defendant and ruin the professional reputation of his counsel.
5 Conclusions
Setting a defence for a computer-crime trial varies greatly depending on when the lawyer is involved in the case. If he is called in during the investigation, he can understand more easily the direction the prosecutor might take. If, on the other hand, the lawyer intervenes just before the trial, his options are more limited because he can only act based on what the prosecution has done, with a limited possibility of a parallel investigation.
In both cases, though, the protocol to follow is the same:
· understand the client’s criminological profile,
· carefully analyse the technical activities of the police and look for prosecution’s mistakes,
· chose whether to adopt a procedural defence, challenge the merits of the accusations or both.
In general terms, the goals of a procedural defence are:
· challenge the integrity of the computer and data chain of custody,
· challenge the lack of compliance of law enforcement and prosecution’s experts with computer forensics best practices,
· attack the way ISP’s traffic data have been collected and analysed,
· expose the behaviour of police officers during undercover activities.
The choice to set the trial exclusively on procedural defence is hazardous because it is seen as an admission of guilt and therefore introduces a negative prejudice in the mind of the judge. Nevertheless, the procedural defence matters because it commands respect for the due process and the rule of law. This is the way the procedural arguments should be presented to push back the perception in the judge’s mind that the counsel is in a desperate condition. Many judges consider procedural defence as a legalistic approach that lawyers push so far that, from the judge’s point of view, go against common sense (Posner, 2010) and therefore cannot be taken in consideration. However, it is also true that while the state has unlimited means and resources, the counsel’s sole weapons are the law and the logic and therefore this ‘legalistic’ approach is the only one that can guarantee a level plain field.
Challenging the merit of the accusations ranges from the exposing uncertainty of the defendant’s identity to the lack of evidence of the mens rea required by the incriminating provision, to the inconsistencies of the modus operandi. Moreover, such kind of defence may be limited to highlighting shortcomings in the evidence gathered by the prosecutor and the technical inconsistencies in the law enforcement’s expertise. Unlike procedural defence, however, in this case, it is more difficult to give general indications because much depends on the specific way in what the specific laws change from one jurisdiction to another.
Putting the strategy into action, the counsel must manage the relationship with the judge with extreme care, avoiding highlighting his limited knowledge of technological aspects, restraining from adopting a professorial attitude and above all not exploiting the ignorance of the judge to confuse him.
These brief considerations do not exhaust such a vast and complex issue as the criminal defence of a computer criminal. They represent, however, a basis on which improve the professional capability and to protect the rule of law and the due process without which there would be no justice on Earth.
References
Barlow, J. (1996). A Declaration of the Independence of Cyberspace. Available at https://www.eff.org/cyberspace-independence visited Aug. 3, 2020.
Chiccarelli, S., Monti, A. (1997-2011) Spaghetti Hacker. Pescara (IT), Monti&Ambrosini editori.
Dershowitz, A. (1983) The Best Defense. New York (NY-USA) Vintage Books.
Jarrett, M., Bailie, M., Hagen, E., Judish, N. (2009). Searching and Seizing Computers and Obtaining Electronic Evidence in Criminal Investigations. Office of Legal EducationExecutive Office forUnited States Attorneys. Available at https://www.justice.gov/sites/default/files/criminal-ccips/legacy/2015/01/14/ssmanual2009.pdf visited Aug. 4, 2020.
Kennealy, E., Monti. A. (2005). Case study: a failure in success’ clothing. Digital Investigation Journal (2005) Issue 2, p. 251
Levy, S. (2010) Hackers: Heroes of the Computer Revolution. Sebastopol (CA-USA), O’Reilly Media.
McCombie, S. et al. (2009). Cybercrime Attribution: An Eastern European Case Study. Proceedings of the 7th Australian Digital Forensics Conference. p. 13.
Monti, A. (2004). The Legal Duty of IAPs to Preserve Traffic Data: A Dream or a Nightmare? International Review of Law, Computers & Technology, Vol. 18, N. 2. p. 223
Mungo, P., Clough, B. (1993). Approaching Zero: The Extraordinary Underworld of Hackers, Phreakers, Virus Writers, and Keyboard Criminals. New York (NY-USA) Random House.
Posner, L. (2010). How Judges Think. Cambridge (MA-USA), Harvard University Press.
Stallman, R. (1985). GNU Manifesto. Dr. Dobb’s Journal of Software Tools Volume 10, Number 3, March, 1985. Available at http://ftp.math.utah.edu/pub/tex/bib/dr-dobbs-1980.html#Stallman:1985:GM visited Aug. 3, 2020.
The Mentor. (1986). The Conscience of a Hacker. Phrack Magazine. Jan. 8, 1986. Available at http://www.phrack.org/archives/issues/7/3.txt visited Aug. 3, 2020.
Winkler, I. (1997). Corporate Espionage. Roseville (CA-USA), Prima Publishing.